Creating a Scalable Security Architecture upon AWS with Cisco Protected AWS plus Firewall Transit Gateway
Comprehensive cloud support is vital when effective and agile security at scale is necessary. With Cisco Secure Firewall Risk Defense 7.1, we’ve added assistance for the AWS Gateway Load Balancer (GWLB) to operate a vehicle basic, agile, and efficient safety within the cloud. This integration simplifies insertion of Cisco Secure Firewall in AWS with Geneve process (RFC 8926) encapsulation. It creates architectures more scalable, partly by removing the necessity for source network deal with translation (SNAT) in the visitors path. Let’s look at a few common make use of cases where this brand new capability is important.
Use-situation: Ingress and Egress visitors inspection
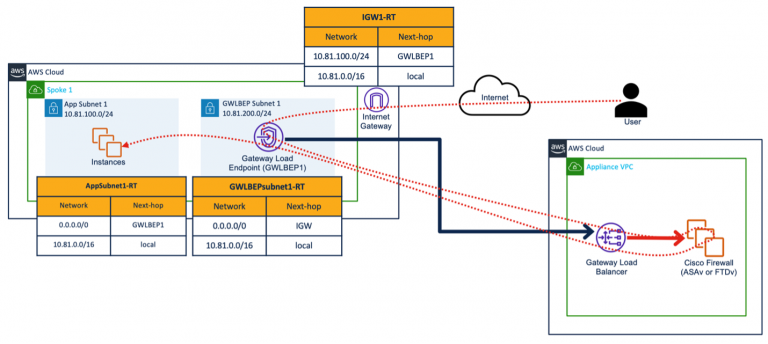
Figure 1 below displays the scalable architecture for protecting ingress visitors making use of Cisco Secure Firewall and AWS Gateway Load Balancer. This architecture recommends developing an appliance VPC having an AWS Gateway Load Balancer and Cisco Protected Firewall virtual devices in the backend swimming pool of the gateway load balancer. Gateway load balancers speak to these firewalls making use of Geneve encapsulation, getting rid of the necessity for SNAT, as packets have got embedded virtual system interface (vni) information.
THE WEB user sends traffic destined to the elastic-IP-address of a workload. Visitors hits the web gateway, and after that it really is redirected to the AWS Gateway Load Balancer Endpoint (GWLBe). The GWLBe transmits visitors to the GWLB, also to the firewall for examination then. Following inspection, the packet is forwarded to the destination workload via GWLBe then.
-
- Ingress Visitors Flow :
Consumer -> IGW -> GWLBe -> GWLB -> Safe Firewall -> GLWB -> GWLBe -> Workload
- Ingress Visitors Flow :

Figure 2 shows the scalable architecture for protecting outbound traffic making use of Cisco Secure AWS and Firewall Gateway Load Balancer. In this Cisco Validated Style, we recommend producing an appliance VPC with a Gateway load balancer and Cisco Protected Firewalls in the backend swimming pool of gateway load balancer. Gateway load balancers speak to these firewalls making use of Geneve encapsulation.
The workload sends traffic to the web. In line with the route table, visitors is usually routed to GWLBe. Visitors gets to the gateway load balancer endpoint once, it forwards visitors to the gateway load balancer in the applying VPC. The gateway load balancer forwards the traffic to Cisco Secure Firewall then. Inspection is complete once, the firewall forwards the traffic to the GWLB back again. The visitors reaches the GWLB as soon as, it transmits it to the GWLBe back, directing the visitors to the Internet.
-
- Egress Visitors Flow :
Workload-> GWLBe -> GWLB -> Safe Firewall -> GLWB -> GWLBe -> Web
- Egress Visitors Flow :

IGW1-RT : This path table is connected to Web Gateway (IGW1) and there exists a route for software subnet (10.81.100.0/24) indicate the gateway load balancer endpoint (GWLBEP).  GWLBEPsubnet1-RT: This path table is related to GWLBEPsubnet1 and there exists a default path that factors to the web Gateway (IGW).
GWLBEPsubnet1-RT: This path table is related to GWLBEPsubnet1 and there exists a default path that factors to the web Gateway (IGW).  AppSubnet1-RT: This path table is linked to AppSubnet1 and there exists a default route that factors to the gateway load balancer endpoint (GWLBEP1).
AppSubnet1-RT: This path table is linked to AppSubnet1 and there exists a default route that factors to the gateway load balancer endpoint (GWLBEP1).  Firewall Construction:
Firewall Construction:
-
- Enable Firewall interface
-
- Associate protection zone to firewall user interface
 VNI User interface configuration:
VNI User interface configuration:
-
- Enable VNI interface and put in a true title for VNI user interface
-
- Create and associate for Security Area on VNI user interface
-
- Enable AWS proxy
-
- Enable VTEP Interface
 Use-situation: Centralized deployment with AWS Transit Gateway (East/West traffic circulation)
Use-situation: Centralized deployment with AWS Transit Gateway (East/West traffic circulation)
Figure 3 displays centralized safety deployment architecture. In this style, AWS Transit Gateway links program VPC to appliance VPC. Transit gateway receives visitors from app VPC and forwards exactly the same to GWLBe (endpoint). GWLBe sends visitors to GWLB, GLWB transmits the visitors to Cisco Secure Firewall. Post firewall inspection, visitors is forwarded back again to the GLWB also to the location VPC via transit gateway then.

Use-situation: Centralized deployment with AWS Transit Gateway (east/west traffic stream)
Figure 4 displays east/west traffic circulation between customer’s Information appliance and Middle VPC.

My next weblog will a deep-dive upon architecture for a centralized deployment design with AWS Transit Gateway and Cisco Protected Firewall within AWS (Body 3 and Figure 4). Keep tuned in!
Additionally, Cisco announced it’ll be supporting Secure Firewall as something on AWS . These enhancements are right section of our dedication to simplify protection across hybrid and multicloud conditions, harmonizing system, workload, and application safety.
Additional assets
Cisco Safe Firewall for Open public Cloud Cisco Protected Firewall on AWS Market At-a-Glance: Cisco Safe Firewall Weblog Announcement: Cisco Protected Firewall as something on AWS
We’d want to hear everything you think. Ask a relevant question, Comment Below, and Remain Linked to Cisco Secure on interpersonal! Cisco Safe Social Channels Instagram
Facebook
Twitter
LinkedIn

You must be logged in to post a comment.