Circular 2 post-quantum TLS is supported within AWS KMS
AWS Key Management Service (AWS KMS) now supports 3 new hybrid post-quantum crucial trade algorithms for the Transportation Layer Security (TLS) 1.2 encryption process that’s used when connecting to AWS KMS API endpoints. These brand new hybrid post-quantum algorithms mix the proven safety of a classical essential exchange with the possible quantum-safe properties of brand new post-quantum important exchanges undergoing assessment for standardization. The fastest of the algorithms adds 0 approximately.3 milliseconds of overheard in comparison to a classical TLS handshake. The brand new post-quantum key swap algorithms added are Circular 2 versions of Kyber, Bit Flipping Key Encapsulation (Bicycle), and Supersingular Isogeny Key Encapsulation (SIKE). Each corporation offers submitted their algorithms to the National Institute of Standards and Technology (NIST) within NIST’s post-quantum cryptography standardization procedure. This process spans many rounds of assessment over multiple yrs, and will probably continue beyond 2021.
Why post-quantum TLS is essential
A large-scale quantum pc can break the existing public-key cryptography that’s useful for key trade in classical TLS connections. While a large-level quantum computer isn’t on the market, it’s still vital that you think about and arrange for your long-term protection needs. Today could possibly be decrypted by way of a large-scale quantum computer later on tls traffic making use of classical algorithms recorded. If you’re developing apps that depend on the long-expression confidentiality of data approved over a TLS link, you should consider an idea to migrate to post-quantum cryptography prior to the lifespan of the sensitivity of one’s data would be vunerable to an unauthorized consumer with a large-level quantum computer. For example, this indicates that if you believe a large-scale quantum computer is usually 25 years away, as well as your data should be secure for twenty years, you need to migrate to post-quantum schemes next 5 years. AWS is attempting to plan this future, and we wish you to too prepare yourself.
We’re providing this feature now rather than looking forward to standardization efforts to end up being complete which means you have ways to gauge the potential performance effect to your applications. Nowadays offering this feature right now also offers you the security afforded by the proposed post-quantum schemes. While we think that the usage of this function raises the already higher security bar allowing you to connect to AWS KMS endpoints, these fresh cipher suites will latency impact bandwidth utilization and. However, using these brand-new algorithms may possibly also create link failures for intermediate techniques that proxy TLS connections. We’d prefer to get suggestions from you on the potency of our execution or any problems found so we are able to improve it as time passes.
Hybrid post-quantum TLS 1.2
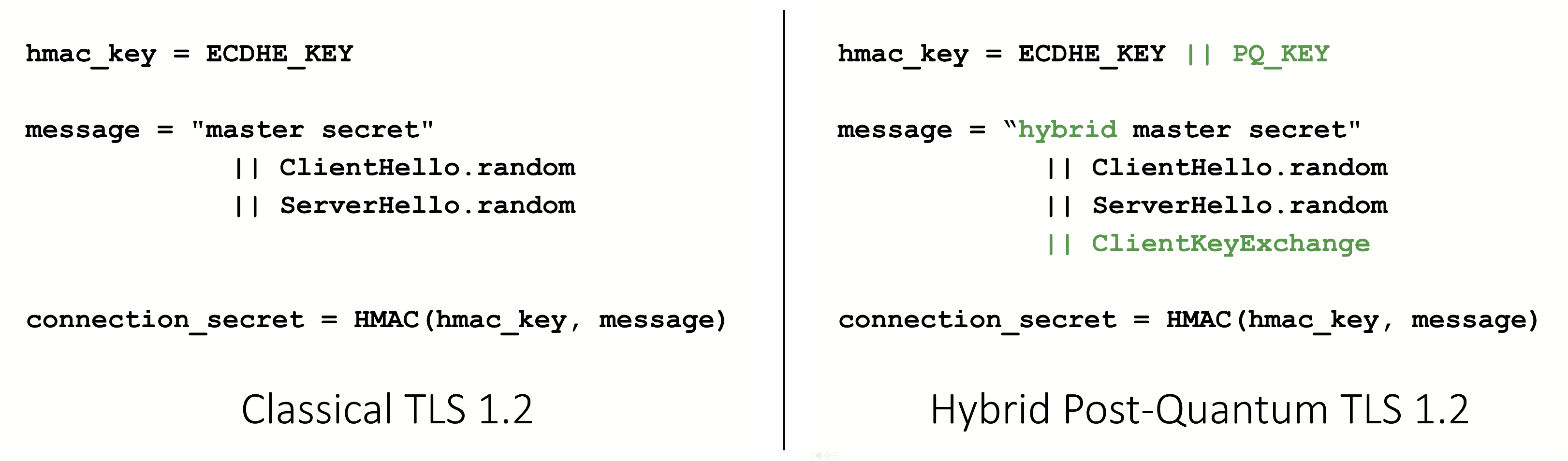
Hybrid post-quantum TLS is really a feature that delivers the security protections of both classical and post-quantum crucial exchange algorithms within a TLS handshake. Figure 1 shows the differences inside the bond secret derivation procedure between hybrid and classical post-quantum TLS 1.2. Hybrid post-quantum TLS 1.2 has three major variations from classical TLS 1.2:
- The negotiated post-quantum essential is appended to the ECDHE essential before being used because the hash-based message authentication code (HMAC) key.
- The text hybrid in its ASCII representation is prepended to the start of the HMAC message.
- The whole client key exchange information from the TLS handshake is definitely appended to the ultimate finish of the HMAC information.

Figure 1: Distinctions in the bond secret derivation procedure between classical and hybrid post-quantum TLS 1.2
Some background on post-quantum TLS
Nowadays, all requests to AWS KMS make use of TLS with key swap algorithms offering perfect forward secrecy and use among the following classical schemes:
While present FFDHE and ECDHE schemes use perfect forward secrecy to safeguard contrary to the compromise of the server’s long-term key key, these schemes don’t drive back large-scale quantum computers. Later on, a sufficiently able large-scale quantum personal computer could run Shor’s Algorithm to recuperate the TLS session essential of a recorded classical program, and access the info inside thereby. Utilizing a post-quantum key trade algorithm through the TLS handshake protects against episodes from the large-scale quantum computer.
The chance of large-scale quantum computing has spurred the growth of new quantum-resistant cryptographic algorithms. NIST has began the procedure of standardizing post-quantum key encapsulation mechanisms (KEMs). A KEM is really a type of key swap that’s used to determine a shared symmetric essential. AWS has selected three NIST KEM submissions to look at inside our post-quantum efforts:
Hybrid mode means that the negotiated essential is as strong because the weakest important agreement scheme. If among the schemes is damaged, the communications stay confidential. THE WEB Engineering Task Push (IETF) Hybrid Post-Quantum Key Encapsulation Options for Transport Layer Security 1.2 draft describes how exactly to combine post-quantum KEMs with ECDHE to generate fresh cipher suites for TLS 1.2.
These cipher suites work with a hybrid key trade that performs two independent crucial exchanges through the TLS handshake. The main element exchange then cryptographically mixes the keys from each right into a individual TLS session essential. This plan combines the proven safety of a classical essential exchange with the possible quantum-safe properties of brand-new post-quantum key exchanges getting analyzed by NIST.
The aftereffect of hybrid post-quantum TLS on overall performance
Post-quantum cipher suites possess another performance bandwidth and user profile use from traditional cipher suites. AWS provides measured bandwidth and across 2 latency,000 TLS handshakes between an Amazon Elastic Compute Cloud (Amazon EC2) C5n.4xlarge client and the general public AWS KMS endpoint, that have been both in the us-west-2 Region. Your personal performance characteristics varies, and will be determined by your environment, together with your:
-
- Hardware-CPU speed and amount of cores.
- Existing workloads-just how often you contact AWS KMS and how many other work the application performs.
capacity and
- Network-location.
The next table and graphs show latency measurements performed by AWS for several newly supported Round 2 post-quantum algorithms, as well as the classical ECDHE important exchange algorithm utilized by most customers currently.
Figure 2 displays the latency distinctions of most hybrid post-quantum algorithms weighed against classical ECDHE alone, and implies that in comparison to ECDHE alone, SIKE offers 101 milliseconds of overhead approximately, BIKE adds 9 approximately.5 milliseconds of overhead, and Kyber adds 0 approximately.3 milliseconds of overhead.

Number 2: TLS handshake latency at varying percentiles for four crucial exchange algorithms
Figure 3 exhibits the latency variations between ECDHE with Kyber, and ECDHE alone. The addition of Kyber adds 0 approximately.3 milliseconds of overhead.

Number 3: TLS handshake latency at various percentiles, with only best two performing key swap algorithms
The next table shows the quantity of information (in bytes) had a need to complete the TLS handshake for every cipher suite, the common latency, and at varying percentiles latency. All dimensions were gathered from 2,000 TLS handshakes. Enough time had been measured on your client right away of the handshake before handshake was finished, and contains all network transfer period. All connections used RSA authentication with a 2048-bit essential, and ECDHE used the secp256r1 curve. All hybrid post-quantum checks used the NIST Circular 2 versions. The Kyber-512 was utilized by the Kyber check parameter, the BIKE check used the BIKE-1 Degree 1 parameter, and the SIKEp434 parameter was utilized by the SIKE test.
ItemBandwidth
(bytes)Total
handshakesAverage
(ms)p0
(ms)p50
(ms)p90
(ms)p99
(ms)ECDHE (basic)3,5742,0003.082.073.023.954.71ECDHE + Kyber R25,8982,0003.362.383.174.285.35ECDHE + Bicycle R212,4562,00014.9111.5914.1618.2723.58ECDHE + SIKE R24,6282,000112.40103.22108.87126.80146.56
By default, the AWS SDK customer performs a TLS handshake to create a fresh TLS connection once, and reuses that TLS link for several requests then. Which means that the increased expense of a hybrid post-quantum TLS handshake will be amortized over several requests sent on the TLS connection. You need to consider the amortization into consideration when evaluating the entire additional cost of making use of post-quantum algorithms; otherwise performance information could be skewed.
AWS KMS has chosen Kyber Circular 2 to end up being KMS’s highest prioritized post-quantum algorithm, with Bicycle Circular 2, and SIKE Circular 2 next in concern order for post-quantum algorithms. The reason being Kyber’s efficiency will be closest to the classical ECDHE functionality that a lot of AWS KMS clients are employing today and are familiar with.
How to utilize hybrid post-quantum cipher suites
To utilize the post-quantum cipher suites with AWS KMS, you will need the preview release of the AWS Common Runtime (CRT) HTTP customer for the AWS SDK for Java 2.x. Furthermore, you will have to configure the AWS CRT HTTP customer to utilize the s2n post-quantum hybrid cipher suites. Post-quantum TLS for AWS KMS comes in all AWS Areas aside from AWS GovCloud (US-East), AWS GovCloud (US-West), AWS China (Beijing) Area managed by Beijing Sinnet Technologies Co. Ltd (“Sinnet”), and AWS China (Ningxia) Area managed by Ningxia Western Cloud Information Technologies Co. Ltd. (“NWCD”). Since NIST have not standardized post-quantum cryptography however, connections that want Federal Information Processing Standards (FIPS) compliance cannot utilize the hybrid key trade. For instance, kms.
.amazonaws.com works with the usage of post-quantum cipher suites, whilst kms-fips. .amazonaws.com will not.
- If you’re utilizing the AWS SDK for Java 2.x, you need to add the preview discharge of the AWS Standard Runtime customer to your Maven dependencies.
- You then must configure the brand new SDK and cipher suite in the prevailing initialization code of one’s application:
Now, all connections designed to AWS KMS inside supported Regions shall utilize the new hybrid post-quantum cipher suites! To visit a complete exemplory case of everything established up, browse the example application here.
Things to attempt
Here are a few ideas around how to utilize this post-quantum-enabled client:
- Work load benchmarks and testing. These fresh cipher suites perform than traditional essential exchange algorithms differently. You may want to adjust your link timeouts to permit for the much longer handshake times or, if you’re running in a AWS Lambda functionality, extend the execution timeout environment.
- Attempt connecting from various locations. According to the network route your request takes, you might find that intermediate hosts, proxies, or firewalls with deep packet inspection (DPI) block the demand. This could be because of the brand-new cipher suites in the ClientHello or the bigger key exchange messages. If this is actually the full case, you might want to utilize your security group or IT administrators to upgrade the relevant construction to unblock the brand new TLS cipher suites. We’d prefer to listen to from you about how exactly your infrastructure interacts with this particular fresh variant of TLS visitors. When you have feedback or questions, please start a brand-new thread on the AWS KMS discussion forum.
Conclusion
In this blog write-up, I announced help for Round 2 hybrid post-quantum algorithms in AWS KMS, and demonstrated you how to get started tinkering with hybrid post-quantum key exchange algorithms for TLS when connecting to AWS KMS endpoints.
More info
If you’d prefer to find out more about post-quantum cryptography have a look at:
Should you have feedback concerning this post, submit remarks in the Comments section below.
Want a lot more AWS Security how-to articles, news, and show announcements? Stick to us on Twitter.
