Nowadays, “cybersecurity” may be the buzzword du jour , infiltrating every organization, invited or even not. Furthermore, this is actually the full case all over the world, where a growing proportion of all solutions have an online business, prompting companies to reconsider the safety of these systems. This, however, isn’t news to Cisco, once we […]
Read more
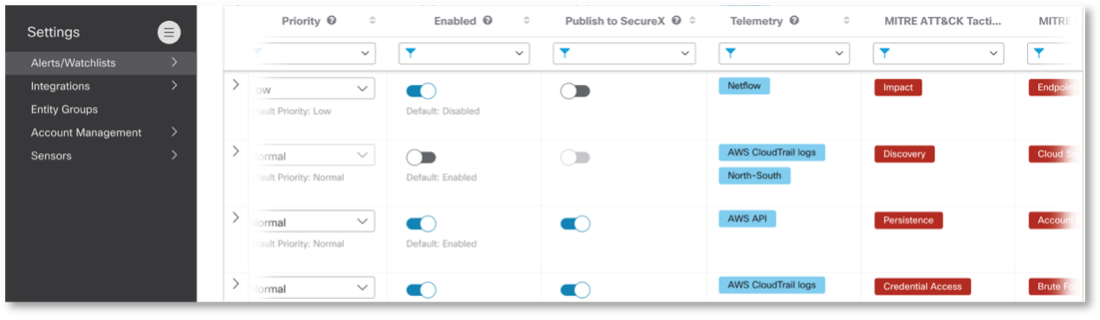
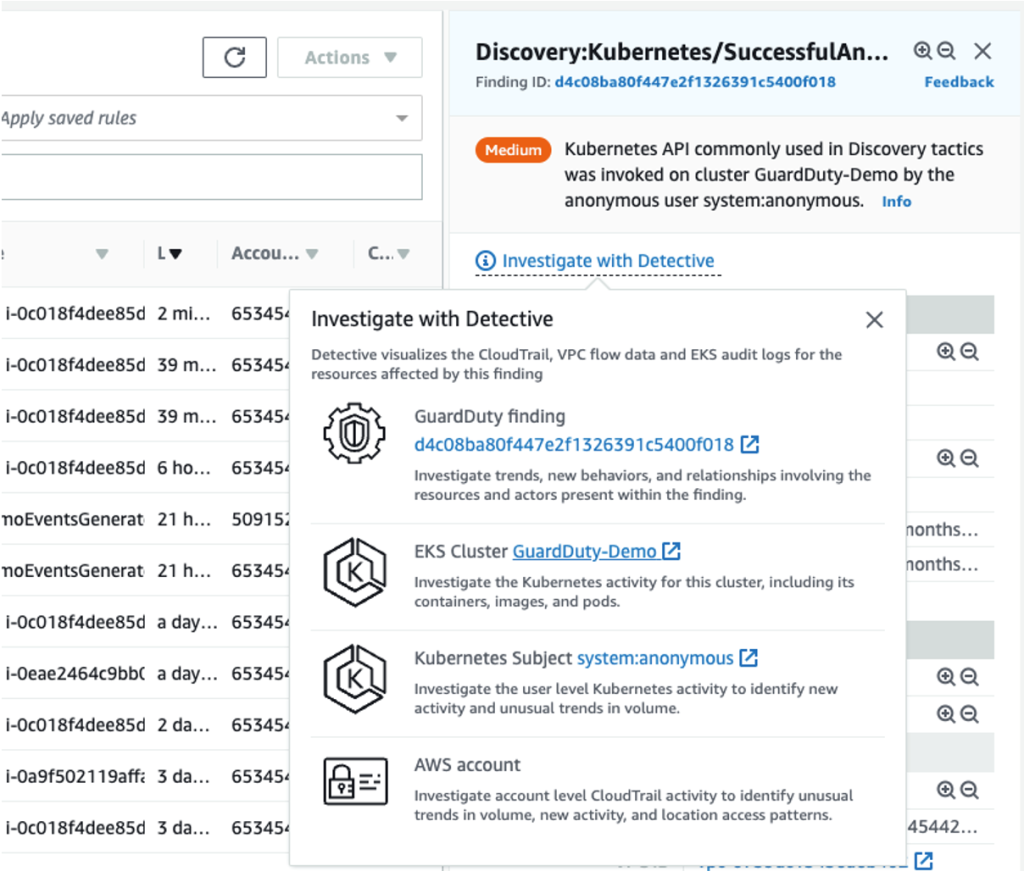
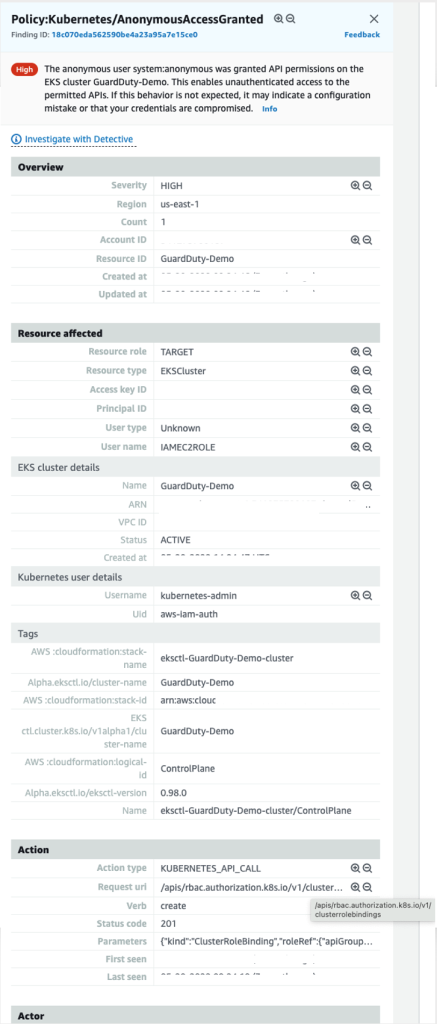



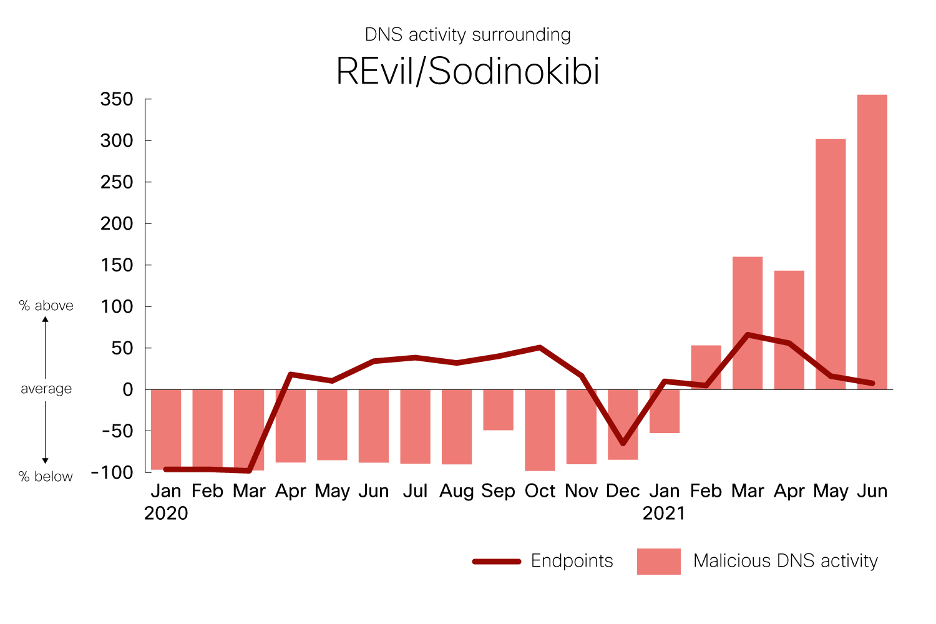


You must be logged in to post a comment.