People, technology and procedure will be the triad for cybersecurity technique. Too often we concentrate on the technology battle and part to respond when failures occur or assaults are successful. Often there’s dilemma and delay because procedures aren’t documented too, groups are siloed and incompatible or possibly, worse, assumptions are created regarding responsibility. In a […]
Read more
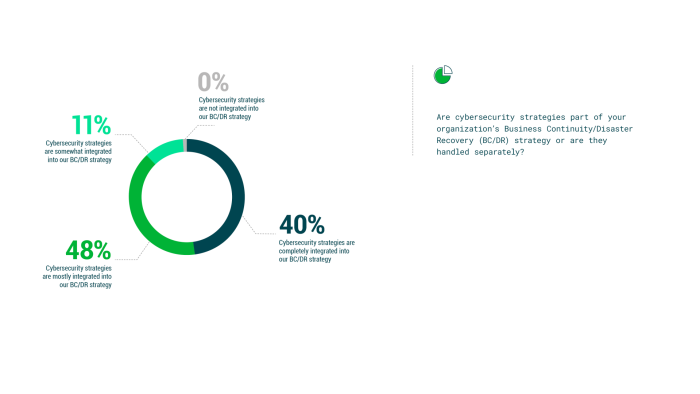






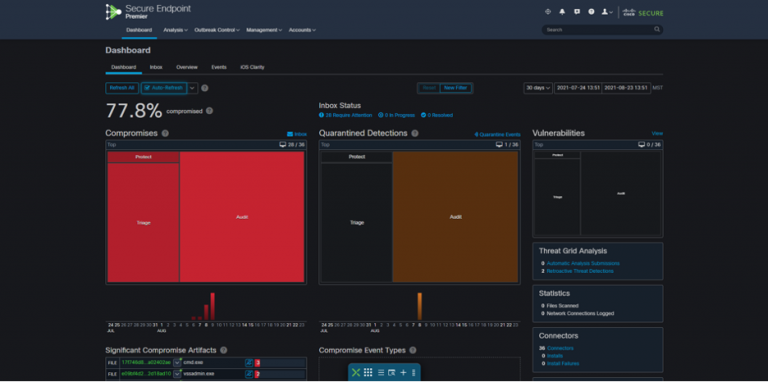


You must be logged in to post a comment.