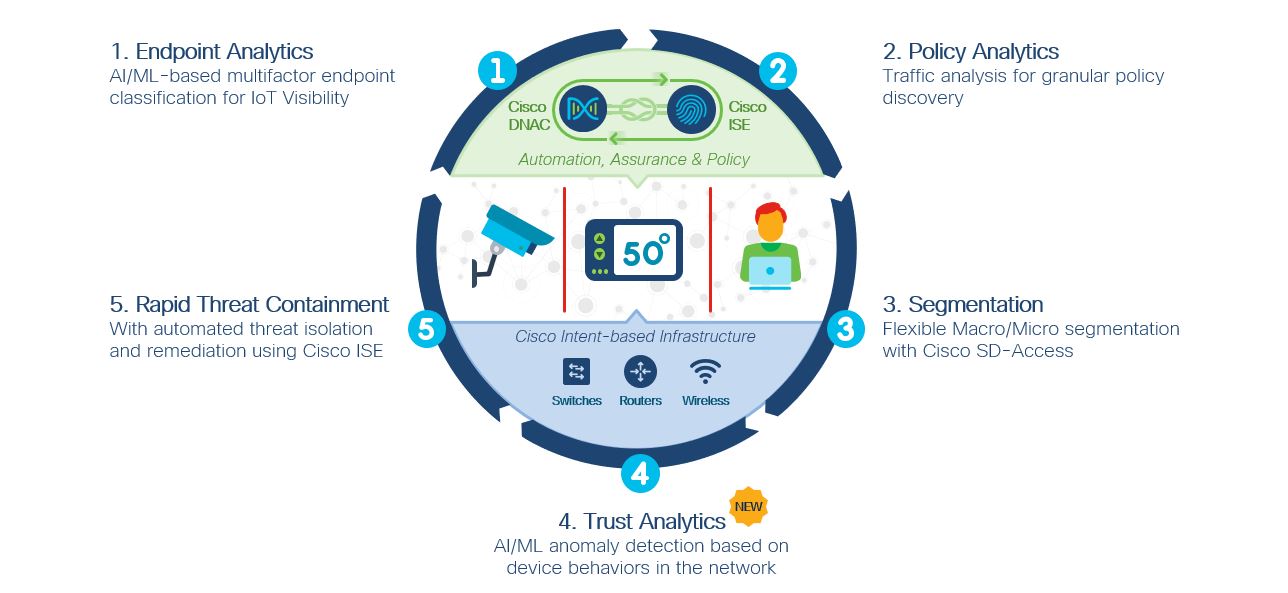
If you’re preparing the working office for the gradual return of workers, you may be adding sensors to monitor environmental conditions, track employee movements, and increase visibility of critical assets. Or you’re rearranging any office space in order to rotate the same workshop between differing people on different days. Or you’re busy adding more video […]
Read more





You must be logged in to post a comment.