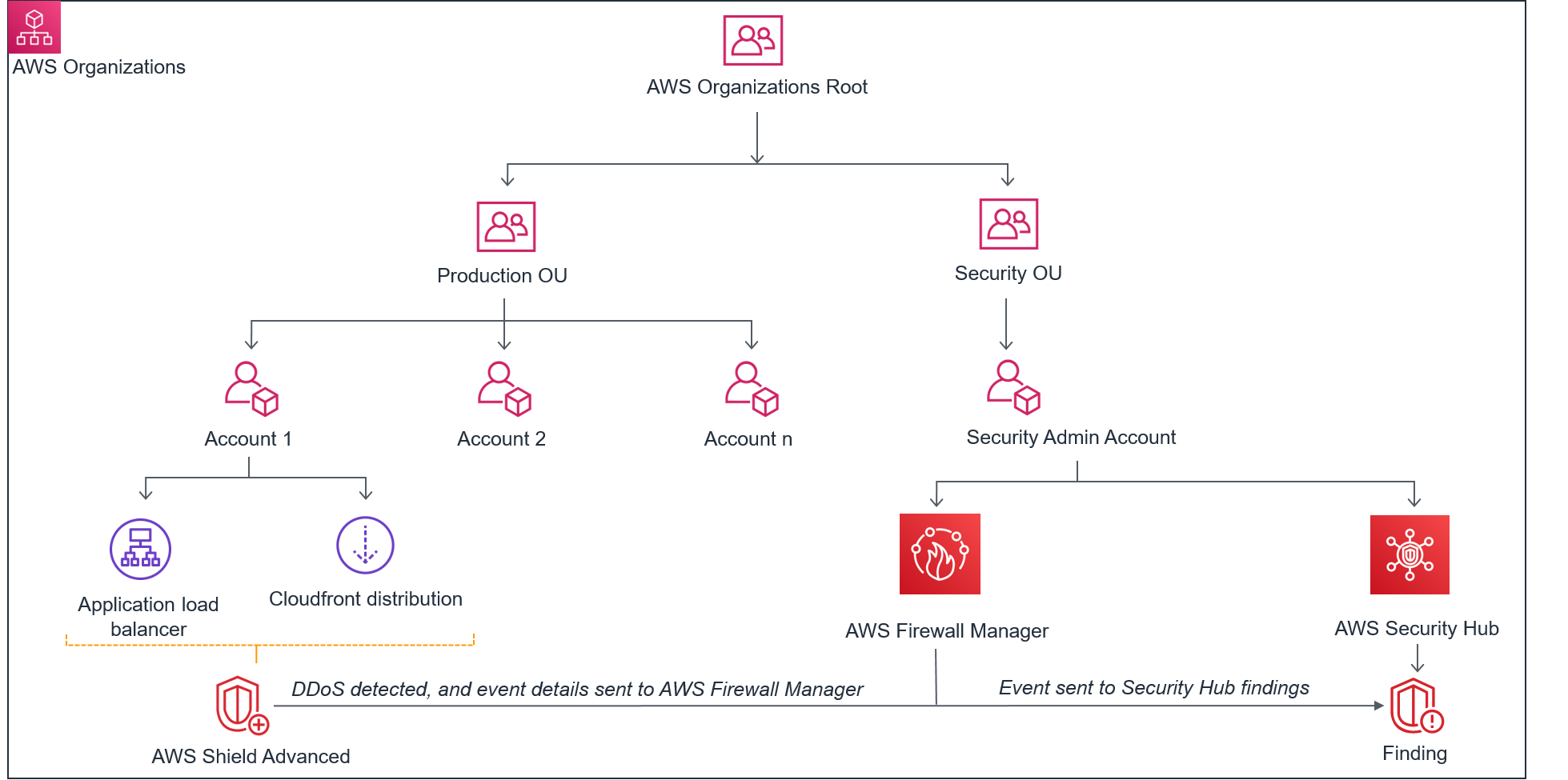
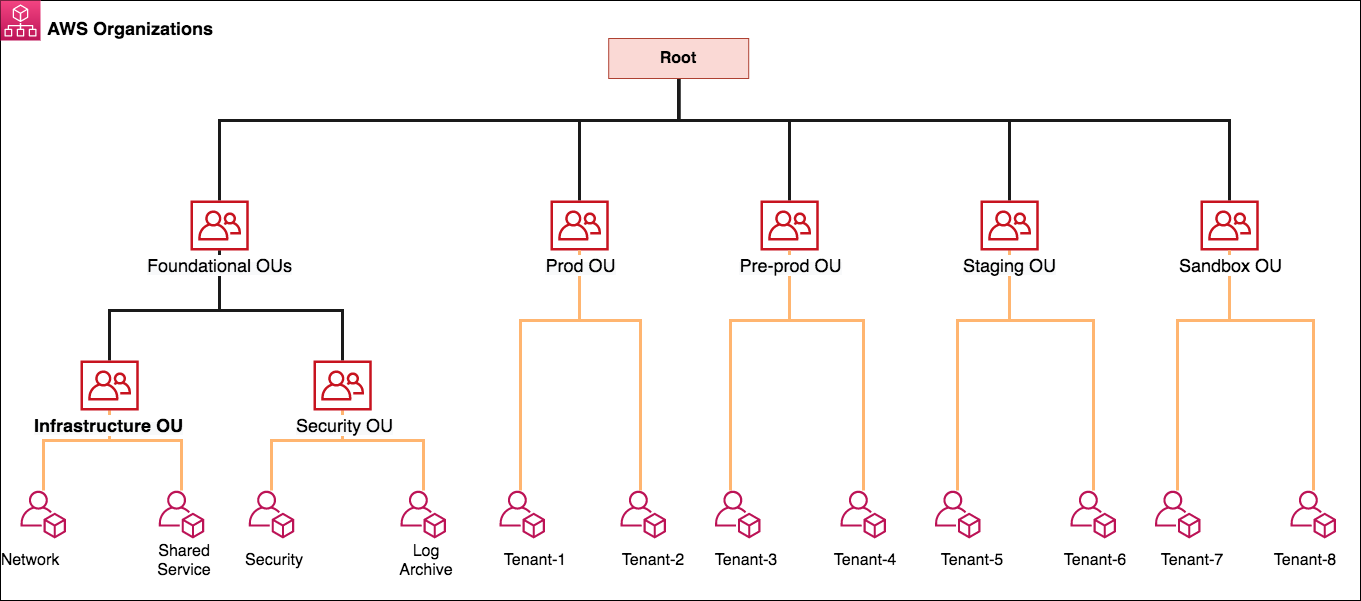
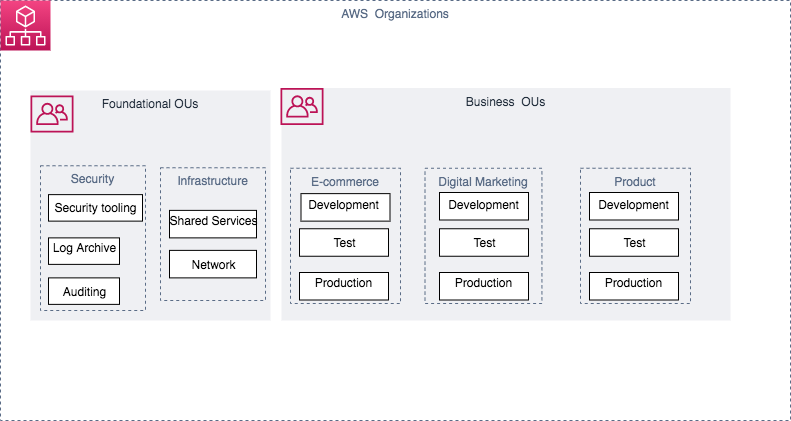
Once you build applications upon Amazon Web Providers (AWS), it’s a common security practice to isolate production resources from non-production resources by logically grouping them into useful units or organizational devices. There are several benefits to this process, such as rendering it easier to put into action the principal of minimum privilege, or decreasing the […]
Read more




You must be logged in to post a comment.