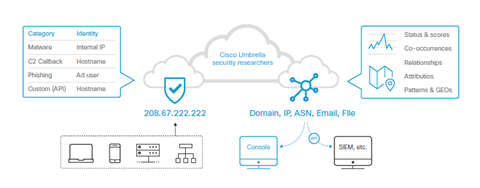
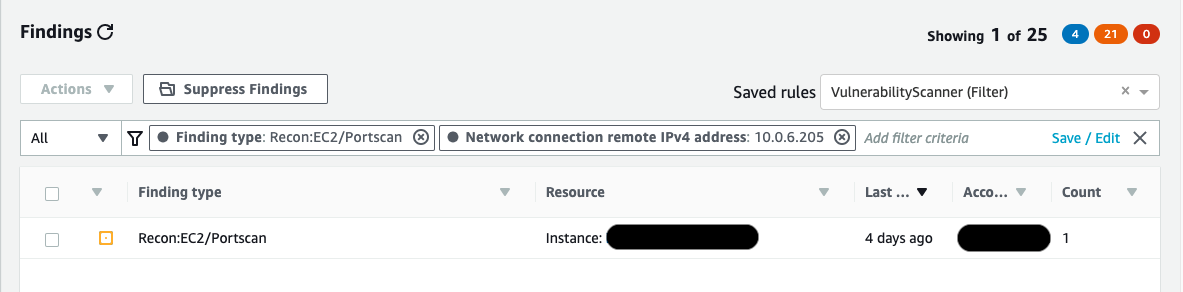
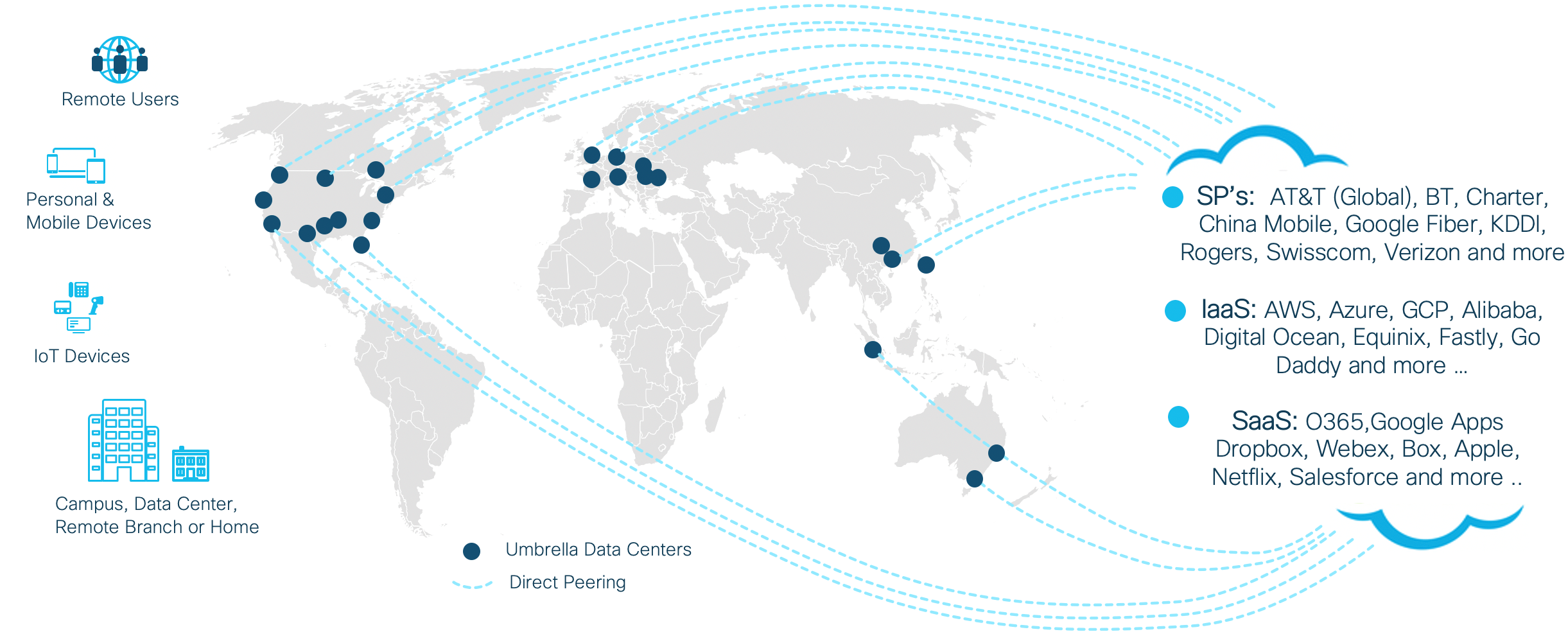
We’ve some exciting news! Soon you’ll have a DevNet sandbox for just one of our Cloud safety solutions: Umbrella. In this website I will walk you through almost all that people have developed within the last few months. In the event that you don’t like reading right now, or in order to know more even, […]
Read more





You must be logged in to post a comment.