<div> <img src=”https://infracom.com.sg/wp-content/uploads/2022/06/reinforce-blog-graphic.png” class=”ff-og-image-inserted” /> </div> I’d prefer to personally invite one to attend the Amazon Web Providers (AWS) security meeting, AWS re:Inforce 2022 , in Boston, On July 26-27 ma. This event presents interactive educational content material to handle your security, compliance, personal privacy, and identity management requirements. Join security experts, clients, leaders, and […]
Read more



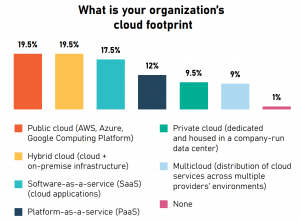





You must be logged in to post a comment.