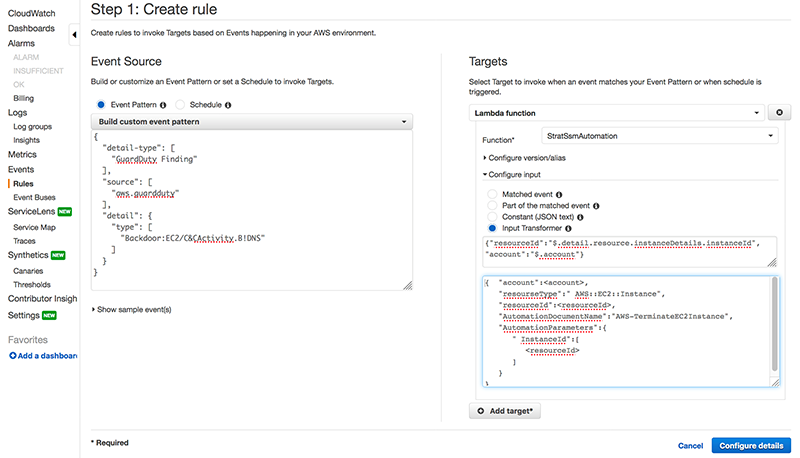
How quickly you react to security incidents is paramount to minimizing their impacts. Automating incident reaction can help you scale your features, decrease the scope of compromised sources rapidly, and reduce repetitive function by security teams. However when you make use of automation, you need to manage exceptions to standard response procedures also. In this […]
Read more



You must be logged in to post a comment.