AWS Firewall Supervisor helps automate security team management: 3 scenarios
In this article, we walk you through scenarios that use AWS Firewall Manager to centrally manage security groupings across your AWS Organizations execution. Firewall Manager is really a security management device that can help you centralize, configure, and keep maintaining AWS WAF rules, AWS Shield Advanced protections, and Amazon Virtual Private Cloud (Amazon VPC) security organizations across AWS Companies.
A multi-account strategy supplies the highest degree of resource isolation, and allows you to track costs and steer clear of jogging into any API limitations efficiently. Creating a separate take into account each project, business device, and development phase enforces logical separation of one’s resources also.
As organizations innovate, designers are updating apps and constantly, in the process, establishing new resources. Managing safety groups for new assets across several accounts becomes complex because the organization grows. Make it possible for developers to possess control on the configuration of these own applications, you may use Firewall Supervisor to automate the auditing and administration of VPC security groupings across multiple Amazon Web Services (AWS) accounts.
Firewall Manager allows you to create security team policies and automatically implement them. You can certainly do this across your complete organization, or restriction it to specified accounts and organizational units (OU). Also, Firewall Supervisor enables you to use AWS Config to recognize and review sources that don’t adhere to the security group plan. It is possible to elect to view the assets and accounts which are out of compliance without using corrective action, or even to remediate noncompliant sources automatically.
Scenarios where AWS Firewall Supervisor might help manage security organizations
Scenario 1: Main security group administration for required security groupings
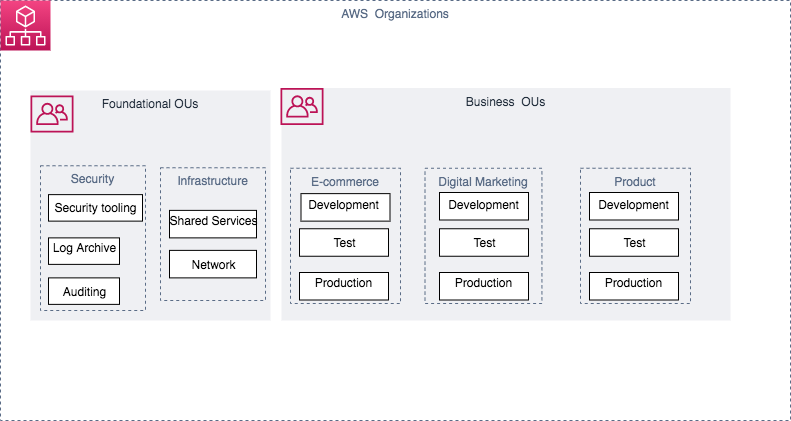
Let’s consider a good example where you’re working an ecommerce site. You’ve made a decision to use Organizations to centrally manage billing and many areas of access, compliance, protection, and sharing assets across AWS accounts. As demonstrated in the following shape, AWS accounts that participate in the same group are usually grouped into OUs. In this instance, the organization includes a foundational OU, and several business OUs-ecommerce, digital advertising, and product.

Figure 1: Summary of ecommerce website
The continuing company OUs support the development, test, and production accounts. Each one of these accounts will be managed by the programmers responsible for development, test, and creation stages useful for the start of the ecommerce website.
The product teams have the effect of configuring and maintaining the AWS environment based on the guidance from the security team. An intrusion recognition program (IDS) has been create to keep track of infrastructure for security action. The IDS architecture demands that an realtor be set up on instances across several accounts. The IDS real estate agent working on the Amazon Elastic Compute Cloud (Amazon EC2) instances shields their infrastructure from typical security issues. The agent collects telemetry data useful for evaluation, and communicates with the main IDS example that sits in the AWS safety account. The main IDS example analyzes the telemetry information and notifies the administrators using its findings.
For the host-based agent to communicate correctly with the central system, each Amazon EC2 instance will need to have particular inbound and outbound ports and particular destinations thought as allowed. Make it possible for our product to spotlight their applications, you want to make use of automation to make sure that the right network construction is implemented in order that instances can talk to the central IDS.
It is possible to address the preceding problem with Firewall Manager by implementing a common security group policy for required accounts. With Firewall Supervisor, you develop a common IDS protection group in the main safety accounts and replicate it across additional accounts in the ecommerce OU, as proven in the next figure.

Figure 2: Security organizations central administration with Firewall Manager
Changes designed to these security groups could be propagated to all or any the accounts seamlessly. The changes could be tracked from the Firewall Manager console as shown inside figure 3. Firewall Supervisor propagates adjustments to the security groupings in line with the tags mounted on the Amazon EC2 instance.
As shown in body 3, with Firewall Supervisor you can quickly see the compliance position for every policy by considering how many accounts are usually contained in the scope of the plan and just how many out of these are compliant or even non-compliant. Firewall Manager can be integrated with AWS Security Hub, that may trigger security automation predicated on findings.

Figure 3: Firewall Manager results
Situation 2: Clean-up of unused and redundant protection groups
Firewall Manager may also help manage the clean-upward of unused and redundant security organizations. In a development atmosphere, instances are terminated article testing often, however the security groups connected with those instances might remain. You want to only take away the security groups which are no longer used to avoid causing problems with running applications.

Figure 4: Ecommerce OU, accounts, and security groups
In our illustration, developers are testing functions in a test account. In this situation, the tests is completed once, the instances are usually terminated and the safety groups stay in the accounts. The preceding physique shows unused security groupings like Test1, Check2, and Check3 in the check account.
Situation 3: Audit and remediate overly permissive security organizations across all AWS accounts
The security team is in charge of maintaining the security of the AWS environment and must monitor and remediate overly permissive security groups across all AWS accounts. Auditing security groupings for overly permissive accessibility is really a critical security perform and will become inefficient and frustrating when done manually.
You may use Firewall Manager content audit security group plan to supply auditing and enforcement of one’s organization’s security plan for risky security organizations, most referred to as allowed or blocked security group rules commonly. This enables one to set guardrails and monitor for permissive rules centrally overly. For example, we established an allow list plan to permit secure shell access just from certified IP addresses on the organization network.
Firewall Manager allows you to create security team policies to safeguard all accounts across your company. These policies are put on accounts or even to OUs that contain particular tags, as demonstrated in figure 5. Utilizing the Firewall Manager gaming console, you can get an instant look at of the non-compliant protection groupings across accounts in your company. Additionally, Firewall Manager could be configured to deliver notifications to the safety administrators or instantly remove non-compliant security organizations.
In the plan scope, it is possible to choose this plan is accounted by the AWS pertains to, the useful resource type, and which source to include in line with the resource tags, as proven in figure 5.

Physique 5: Edit tags for plan scope
Conclusion
This post shares several core use cases that enable security practitioners to create the ability to centrally manage security groups across AWS Organizations. Developers can concentrate on building applications, as the configuration and audit of network controls is automated by Firewall Manager. The key use situations we discussed are:
- Common protection group policies
- Articles audit security groupings policies
- Usage audit safety group policies
Firewall Manager pays to in an evergrowing and dynamic multi-accounts AWS environment. Follow the Getting Started with Firewall Manager guide to find out more about implementing this service within your AWS environment.
When you have feedback concerning this post, submit remarks in the Comments section below. Should you have questions concerning this post, start a brand new thread on the AWS Firewall Manager forum or contact AWS Support.
Want a lot more AWS Security how-to articles, news, and show announcements? Stick to us on Twitter.
