Avoiding Log4j with Protected Firewall & Secure IPS
The Apache Log4j vulnerability (CVE-2021-44228) has had the web by storm during the past few times. This website details quick ways Safe Firewall Threat Protection (FTD) and Protected IPS users can drive back assaults leveraging this vulnerability while patching their infrastructure.
On Friday talos very first released updated Snort guidelines, December 10. For clients inspecting ingress visitors- with decryption if visitors is TLS (Transport Level Security) encrypted – these guidelines will alert and will block attacks predicated on this vulnerability. Relevant Snort 2 guidelines are 58722-58744, 58751 and Snort 3 guidelines 300055-300058. Saturday and you will be updated once again on Monday new recognition was released, December 13. Clients should continue to look for Snort rule updates away of band via guide or automatic updates since needed. Checking for brand new Snort SRU/LSP improvements at the very least daily is recommended.
Listed below are further actions you can take to mitigate the chance of compromise.
Take note : The ways below show a good example of how exactly to use Correlation guidelines and policy to supply enhanced visibility into uncommon or suspicious action. The example isn't meant to become all encompassing for the Log4j vulnerability as extra attack vectors have already been identified since this short article was published. Readers should utilize the examples below to generate their very own environment specific customized rules predicated on up-to-date threat intelligence.
While information concerning the attack methods is evolving still, the most typical vectors involve a vulnerable server accessing a malicious LDAP server to be fully exploited. With this thought, here are measures that Cisco Secure Firewall Risk Defense network and safety administrators may take to mitigate episodes on their systems
Step one 1
Prevent unnecessary outbound connections from DMZ servers. That is something that ought to be in place as an over-all security practice already. For this circumstance, add an Access Manage rule to prevent outbound connections from your own DMZ hosts on the LDAP slot – 389/tcp. Going additional by blocking all unwanted outbound connections can be an better way even, since all the possible attack vectors aren’t fully known especially. However, in case you are concerned about impacting existing company processes, you might like to at least focus on LDAP connections.
Enable logging because of this monitor and rule for just about any attempts by your servers for connecting to an exterior system. This could be a sign of a operational system that’s under attack.
If you fail to block outbound connections, another steps shall allow supervising for these connections. This can not stop the strike, but will notify you that follow-up action may be required.
Step two 2
Enable outbound connection logging for the DMZ hosts or various other vulnerable systems potentially.
Link logging can be extremely high volume, so it’s important to end up being selective, but we are in need of connection activities for the next phase to work. One method to do this would be to add an Accessibility Control Monitor principle to log your outbound connections from these techniques. A Monitor guideline is a safe method to add a principle to the Access Manage policy without impacting visitors flow. Monitor rules just provide link logging , nor impact processing by some other Access Control rules. Make sure to specify your DMZ web host IP addresses/ranges because the source because of this rule and stick it high sufficient that visitors from your own DMZ systems will strike it.
Step three 3
Develop a Correlation Rule that creates for just about any 389/TCP connections initiated from DMZ hosts to anywhere. Add suitable alerting to this guideline to notify of possible compromise.
Correlation guidelines provide additional notifications for existing occasions. In this full case, the intent would be to increase a flag any moment we see behaviour from a host that may indicate a compromise. Based on your Firewall Administration Center (FMC) configuration it is possible to send out a SNMP trap, Syslog or email message whenever a Correlation Rule triggers. Furthermore, when enabled, these guidelines will create Correlation events within the FMC always.
Quick steps to generate such a rule:
Navigate to Plans -> Correlation -> Principle Management.
Create a rule.
Give it a genuine name.
Select Link event for the function enter the If drop-down.
You will probably desire to limit this principle to connections from specific hosts to the LDAP port. To get this done, add circumstances for the IP ranges and for the interface.
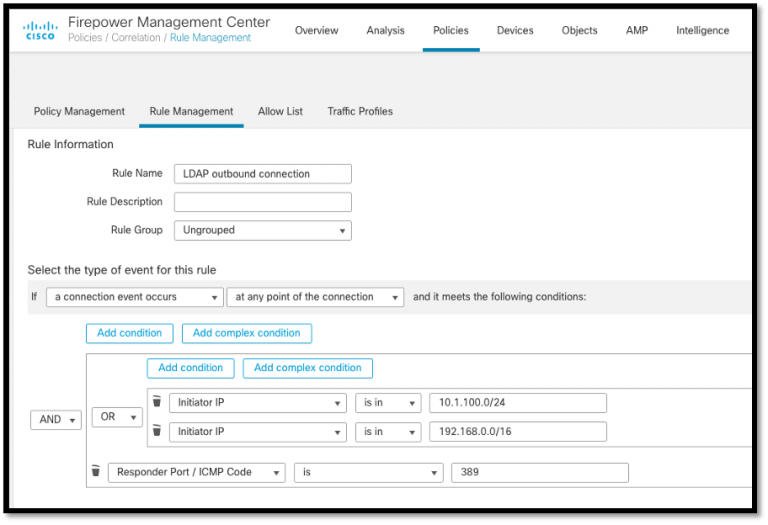
In Connection events your client (your DMZ server in cases like this) is named the Initiator, so develop a condition which will be real for connections initiated from these hosts. It could read something similar to “Initiator IP will be in 10.0.0.0/24” – get into your personal IP range right here. If you want to add multiple supply IP ranges, utilize the “Add Complex Problem” option. After that you can add multiple condition guidelines utilizing the OR operator to add multiple network ranges.
Add a condition with regard to the Responder Interface 389 then. This would utilize the AND operator combined with source IP ranges additional above.
In the final end, your rule can look something like this:

Lastly, create or add this rule to a Correlation policy and enable eternal alerting because needed.
Cisco includes a YouTube movie describing Correlation Plan and rule development available here: https://www.youtube.com/watch?v=bfqSUTLGHyY&t=3s
Stay abreast of more developments through the Talos Blog web page here: https://weblog.talosintelligence.com/
Following steps above might help mitigate and/or even alert for malicious actions surrounding the particular Log4j vulnerability.
Additional Assets
Cisco Talos Log4j Advisory Cisco Occasion Reaction: Apache Log4j Java Logging library

You must be logged in to post a comment.