Automated and safe domain membership administration for EC2 instances without internet access
In this website post, I demonstrate how exactly to deploy an automated solution that can help you fully automate the Energetic Directory join and unjoin procedure for Amazon Elastic Compute Cloud (Amazon EC2) instances that don’t have access to the internet.
Managing Energetic Directory domain membership intended for EC2 instances in Amazon Web Services (AWS) Cloud is really a typical use situation for many organizations. Per day in a powerful environment that may grow and shrink several times, adding and removing personal computer objects from a dynamic Directory domain is really a critical job and is tough to control without automation.
AWS seamless domain join offers a safe and reliable substitute for join an EC2 instance to your AWS Directory Service for Microsoft Active Directory. It’s a recommended method for automating signing up for a Windows or Linux EC2 instance to the AWS Managed Microsoft AD or even to an existing on-premises Energetic Directory making use of AD Connector, or perhaps a standalone Simple AD directory operating within the AWS Cloud. This technique requires your EC2 situations to possess connectivity to the general public AWS Directory Service endpoints. At the proper time of writing, Directory Service doesn’t possess PrivateLink endpoint support. This implies you must allow visitors from your own instances to the general public Directory Services endpoints via an web gateway, network deal with translation (NAT) device, digital private network (VPN) link, or AWS Direct Connect connection.
At times, your company may need that any traffic in the middle of your VPC and Directory Service-or any AWS service-not leave the Amazon network. Which means launching EC2 situations within an Amazon Virtual Private Cloud (Amazon VPC) without internet access but still having to join and unjoin the situations from the Energetic Directory domain. Supplied your situations have network online connectivity to the directory DNS addresses, the easiest solution in this situation is to operate the domain join instructions manually on the EC2 situations and enter the domain credentials straight. Though this process could be secure-as you don’t have to shop or hardcode the credentials-it’s frustrating and becomes hard to control in a dynamic atmosphere where EC2 situations are released and terminated frequently.
VPC endpoints enable private connections in the middle of your VPC and supported AWS providers. Personal connections allow you to access services through the use of personal IP addresses privately. Traffic between your VPC along with other AWS solutions doesn’t keep the Amazon network. Instances within your VPC don’t need community IP addresses to talk to resources in the continuing service.
The solution in this website post uses AWS Secrets Manager to shop the domain credentials and VPC endpoints make it possible for private connection in the middle of your VPC along with other AWS services. The answer described here may be used in the next scenarios:
- Manage domain and unjoin for EC2 situations that don’t have access to the internet join.
- Manage only domain unjoin if you’re using seamless domain sign up for supplied by AWS already, or any other way for domain joining.
- Manage only sign up for for EC2 situations that don’t have access to the internet domain.
This solution uses AWS CloudFormation to deploy the mandatory resources within your AWS account predicated on your decision from the preceding scenarios.
Note: If your EC2 situations can access the web, then we recommend utilizing the seamless domain join function and using scenario 2 to eliminate computers from the Energetic Directory domain upon example termination.
The perfect solution is described in this website post is made to give a secure, automated way for joining and unjoining EC2 instances to an AWS or on-premises Managed Microsoft AD domain. The solution is most effective for use situations where the EC2 situations don’t have internet connection and the smooth domain join option can’t be used.
How this solution functions
This blog post carries a CloudFormation template which you can use to deploy this option. The CloudFormation stack provisions an EC2 Windows example running within an Amazon EC2 Auto Scaling group that acts since a worker and is in charge of joining and unjoining various other EC2 situations from the Active Directory domain. The worker example communicates with some other required AWS providers such as for example Amazon Simple Storage Service (Amazon S3), Secrets Manager, and Amazon Simple Queue Service (Amazon SQS) making use of VPC endpoints. The stack furthermore creates all the other resources necessary for this treatment for work.
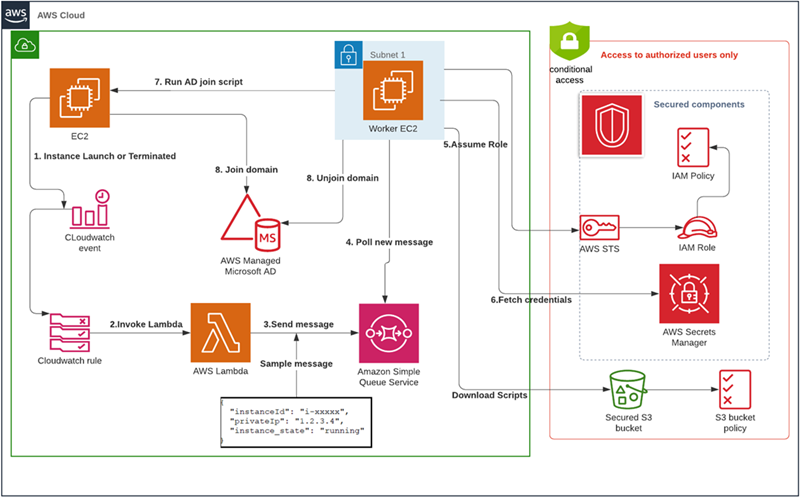
Figure 1 displays the domain and unjoin workflow for EC2 situations within an AWS account join.

Physique 1: Workflow for joining and unjoining an EC2 instance from the domain with complete protection of Energetic Directory credentials
The function flow in Figure 1 is really as follows:
- An EC2 example is terminated or released in an account.
- An Amazon CloudWatch Events guideline detects if the EC2 instance is within working or terminated state.
- The CloudWatch event triggers an AWS Lambda perform that searches for the tag JoinAD: true to check on if the instance must sign up for or unjoin the Energetic Directory domain.
- If the tag value is true, the Lambda function writes the example details to an Amazon Simple Queue Service (Amazon SQS) queue.
- A standalone, highly secured EC2 instance functions as an employee and polls the Amazon SQS queue for brand new messages.
- Whenever there’s a fresh information in the queue, the employee EC2 example invokes scripts on the remote control EC2 instance to include or remove the example from the domain in line with the instance operating-system and state.
In this solution, the safety of the Energetic Directory credentials is improved by storing them in Strategies Manager. To protected the stored credentials, the answer uses resource-based policies to restrict the usage of only intended roles and users.
The credentials can only just be fetched dynamically from the EC2 instance that’s performing the domain join and unjoin operations. Any usage of that instance is more restricted by way of a custom AWS Identity and Access Management (IAM) policy developed by the CloudFormation stack. The next policies are manufactured by the stack to improve security of the perfect solution is components.
- Resource-based policies for Secrets Supervisor to restrict just about all usage of the stored key to only particular IAM entities (like the EC2 IAM role).
- An S3 bucket policy to avoid unauthorized usage of the Energetic Directory join and remove scripts which are stored within the S3 bucket.
- The IAM role that’s used to fetch the credentials from Techniques Manager is restricted by way of a custom IAM policy and will just be assumed by the employee EC2 instance. This prevents every entity apart from the worker example from making use of that IAM part.
- All API and gaming console usage of the worker EC2 example is restricted by way of a custom IAM policy having an explicit deny.
- A plan to deny all however the worker EC2 example usage of the credentials in Strategies Manager. With the worker EC2 example doing the continuous work, the EC2 situations that need to become listed on the domain don’t require usage of the credentials in Techniques Manager or even to scripts in the S3 bucket.
Prerequisites and set up
Before you deploy the answer, you must complete the next in the AWS account and Region where you intend to deploy the CloudFormation stack.
- AWS Managed Microsoft AD having an appropriate DNS title (for instance, test.com). You may use your on premises Energetic Directory also, supplied it’s reachable from the Amazon VPC over Direct Connect or AWS VPN.
- Create a DHCP option set with on-premises DNS servers or with the DNS servers pointing to the IP addresses of directories supplied by AWS.
- Associate the DHCP option established with the Amazon VPC that you are going to use with this particular solution.
- Any additional Amazon VPCs which are hosting EC2 instances to be domain joined should be peered with the VPC that hosts the appropriate AWS Managed Microsoft AD. Alternatively, AWS Transit Gateway may be used to establish this online connectivity.
- Make certain to really have the latest AWS Command Line Interface (AWS CLI) installed and configured on your own local machine.
- Create a fresh SSH key shop and pair it within Secrets Manager utilizing the following commands. Replace with the spot of one’s deployment. Replace with any customized name or depart it default.
Bash:
PowerShell:
Note: Don’t change the title of the trick, as other scripts within the perfect solution is reference it. The employee EC2 example will fetch the SSH essential using GetSecretValue API to SSH or RDP into various other EC2 instances during domain join procedure.
Deploy the alternative
With the prerequisites set up, your next step would be to download or clone the GitHub repo and shop the files on your own local machine. Visit the place where you downloaded or even cloned the repo and evaluation the contents of the config/OS_Consumer_Mapping.json document to validate the example user name and operating-system mapping. Update the document if you’re utilizing a user name apart from the main one used to get on the EC2 situations. The default user title used in this answer is ec2-consumer for Linux situations and Administrator for Windows.
The solution requires installing some software on the worker EC2 instance. As the EC2 example doesn’t have access to the internet, you must download the most recent Windows 64-bit edition of the next software to your neighborhood device and upload it in to the remedy deployment S3 bucket in subsequent measures.
Note: This task isn’t required if your EC2 instances have access to the internet.
Once done, utilize the following tips to deploy the answer in your AWS accounts:
Measures to deploy the perfect solution is:
- Create an exclusive Amazon Simple Storage Service (Amazon S3) bucket using this documentation to shop the Lambda features and the domain join and unjoin scripts.
- As soon as created, enable versioning with this bucket utilizing the following documentation. Versioning enables you to keep multiple variations of your objects in a single bucket and can help you quickly retrieve and restore earlier versions of one’s scripts.
- Upload the program you downloaded to the S3 bucket. That is just required if your example doesn’t have access to the internet.
- Upload the downloaded or cloned GitHub repo data files to the S3 bucket.
- Move to the S3 bucket and choose the template name secret-active-dir-solution.json, and duplicate the thing URL.
- Open up the CloudFormation console. Pick the appropriate AWS Area, and choose Create Stack then. Select With fresh resources.
- Select Amazon S3 URL because the template supply, paste the thing URL that you copied inside Step 5, and choose Next then.
- On the Specify stack information page, enter a genuine title for the stack and offer the next input parameters. It is possible to modify the default ideals to customize the answer for your environment.
- ADUSECASE – From the dropdown menu, go for your needed use case. There is absolutely no default value.
- AdminUserId – The canonical user ID of the IAM user who manages the Dynamic Directory credentials stored inside Secrets Manager. To understand where to find the canonical consumer ID for the IAM user, scroll right down to Getting the canonical consumer ID for the AWS accounts in AWS account identifiers.
- DenyPolicyName – The title of the IAM policy that restricts usage of the worker EC2 example and the IAM function used by the employee to fetch credentials from Strategies Manager. It is possible to keep carefully the default value or provide another true name.
- InstanceType – Instance kind to be utilized when launching the employee EC2 instance. The default could be kept by you value or use another instance type if necessary.
- Placeholder – It is a dummy parameter that’s utilized as a placeholder inside IAM policies for the EC2 example ID. Keep carefully the default value.
- S3Bucket – The title of the S3 bucket that you created inside step one of the perfect solution is deployment. Replace the default worth together with your S3 bucket title.
- S3prefix – Amazon S3 object important where in fact the source scripts are usually stored. Depart the default value provided that the cloned GitHub directory construction hasn’t been transformed.
- SSHKeyRequired – Select true or false predicated on whether an SSH crucial pair must RDP in to the EC2 worker example. If you select false, the worker EC2 instance shall not need an SSH key pair.
- SecurityGroupId – Security team IDs to be linked to the worker instance to regulate traffic to and from the example.
- Subnet – Choose the VPC subnet where you intend to launch the employee EC2 instance.
- VPC – Choose the VPC where you intend to launch the employee EC2 instance. Utilize the VPC where in fact the AWS has been developed by a person Managed Microsoft AD.
- WorkerSSHKeyName – A preexisting SSH key pair title which you can use to find the password for RDP accessibility in to the EC2 worker example. This isn’t mandatory if you’re using user title and password structured login or AWS Systems Manager Session Manager. That is required only when you have selected true for the SSHKeyRequired parameter.

Number 2: Defining the stack name and insight parameters for the CloudFormation stack
- Enter ideals for several of the insight parameters, and choose Next.
- On the Options page, keep carefully the default ideals and choose Up coming.
- On the Review web page, confirm the details, acknowledge that CloudFormation might create IAM assets with custom names, and choose Create Stack.
- Once the stack development is marked as CREATE_COMPLETE, the next resources are manufactured:
- An EC2 instance that works as an employee and runs Dynamic Directory join scripts on the remote control EC2 instances. It unjoins situations from the domain upon example termination also.
- A key with a default Dynamic Directory domain title, user title, and a dummy password. The real name of the default secret is myadcredV1.
- A Secrets Supervisor resource-based plan to deny all usage of the trick except to the intended IAM customers and roles.
- An EC2 IAM IAM and profile part to be utilized only by the employee EC2 instance.
- The managed IAM plan called DENYPOLICY which can be assigned to an IAM user, group, or function to restrict usage of the solution resources like the worker EC2 example.
- A CloudWatch Events principle to detect jogging and terminated claims for EC2 instances and result in a Lambda function that posts instance information to an SQS queue.
- A Lambda functionality that reads example writes and tags to an SQS queue in line with the instance tag value, which may be or false true.
- An SQS queue for storing the EC2 instance condition-running or even terminated.
- A dead-letter queue for storing unprocessed messages.
- An S3 bucket policy to restrict usage of the foundation S3 bucket from unauthorized roles or users.
- A CloudWatch log team to stream the logs of the employee EC2 instance.
Test the option
That the answer is deployed now, you can attempt it to check on if it’s working needlessly to say. Before the alternative is examined by you, you must demand secret created in Techniques Supervisor by CloudFormation and revise the Dynamic Directory credentials-domain name, consumer name, and password.
To check the solution
- Inside the CloudFormation system, choose Services, and CloudFormation then. Select your stack title. On the stack Outputs tab, search for the ADSecret entry.
- Select the ADSecret connect to visit the configuration for the trick in the Strategies Manager console. Scroll right down to the area titled Secret worth, and choose Retrieve key value to show the default Magic formula Key and Secret Value as shown in Number 3.

Figure 3: Retrieve worth in Secrets Manager
- Choose the Edit button and up-date the default dummy credentials together with your Dynamic Directory domain credentials.(Optional) Directory_ou can be used to shop the organizational device (OU) and directory components (DC) for the directory; for instance, OU=test,DC=illustration,DC=com.
Note: instance_password can be an optional secret essential and is used only once you’re using user title and password based login to gain access to the EC2 instances inside your account.
That the trick is updated with the right credentials now, it is possible to launch a check EC2 instance and determine if the instance offers successfully joined the Dynamic Directory domain.
Generate an Amazon Device Image
Note: That is only necessary for Linux-based operating techniques apart from Amazon Linux. It is possible to skip these actions if your situations have internet access.
As your VPC doesn’t have access to the internet, for Linux-based systems apart from Amazon Linux 1 or Amazon Linux 2, the mandatory packages must be on the instances that require to join the Dynamic Directory domain. For that, you need to develop a custom Amazon Device Picture (AMI) from an EC2 example with the mandatory packages. For those who have a process to create your personal AMIs already, these packages could be added by you within that existing process.
To install the package deal into your AMI
- Create a fresh EC2 Linux example for the required operating-system in a general public subnet or a personal subnet with usage of the internet with a NAT gateway.
- Connect to the example using any SSH customer.
- Install the mandatory software by working the next command that is befitting the operating-system:
- For CentOS:
- For RHEL:
- For Ubuntu:
- For SUSE:
- For Debian:
- Follow Manually join a Linux instance to set up the AWS CLI about Linux.
- Create a fresh AMI predicated on this example by following instructions in Create a Linux AMI from an instance.
You now have a fresh AMI which you can use within the next steps and in potential future to launch similar instances.
For Amazon Linux-based EC2 instances, the perfect solution is will use the system described in How may i update yum or install packages without access to the internet on my EC2 instances to set up the required deals and you also don’t need to develop a custom made AMI. No additional deals are required if you work with Windows-based EC2 instances.
To release a test EC2 example
-
- Navigate to the Amazon EC2 gaming console and launch an Amazon Linux or Windows EC2 instance in exactly the same Area and VPC that you utilized when making the CloudFormation stack. For just about any other operating system, make certain the custom has been utilized by you AMI made before.
- In the Add Tags section, put in a tag named JoinAD and set the worthiness as true. Add another tag called Operating_System and set the correct operating-system value from:
- AMAZON_LINUX
- FEDORA
- RHEL
- CENTOS
- UBUNTU
- DEBIAN
- SUSE
- WINDOWS
- Make sure the security group connected with this instance is defined to permit all inbound targeted traffic from the security band of the employee EC2 instance.
- Make use of the SSH essential pair title from the prerequisites (Action 6) when launching the instance.
- Wait around for the example to start and join the Dynamic Directory domain. Now you can demand CloudWatch log team named /ad-domain-join-solution/ developed by the CloudFormation stack to find out if the example has joined up with the domain or not really. On successful join, it is possible to hook up to the instance utilizing a SSH or RDP customer and getting into your login credentials.
check the domain unjoin workflow
- To, it is possible to terminate the EC2 example launched in Step one 1 and get on the Dynamic Directory tools example to validate that the Dynamic Directory computer item that represents the example is deleted.
Solution review
Let’s review the facts of the answer components and what goes on through the domain join and unjoin procedure:
1) The employee EC2 instance:
The worker EC2 instance found in this solution is really a Home windows instance with all configurations necessary to add and remove devices to and from a dynamic Directory domain. It is also used being an Active Directory administration tools instance. This example is continuously owning a bash script that’s polling the SQS queue for brand-new text messages. Upon arrival of a fresh information, the script performs the next tasks:
- Check out if the example is in running or even terminated state to find out if it must be added or taken off the Dynamic Directory domain.
- If the information is from the launched EC2 instance, then which means that this example must join the Active Directory domain.
- The script identifies the instance operating-system and runs the correct bash or PowerShell script on the remote EC2.
- Likewise, if the example is within terminated state, then your worker will run the domain unjoin command locally to eliminate the computer object from the Active Directory domain.
- If the worker does not process a note in the SQS queue, it sends the unprocessed information to a backup queue for debugging.
- The worker writes logs linked to the failure or achievement of the domain join to a CloudWatch log team. Use /ad-domain-join-solution to filter for several other logs developed by the worker example in CloudWatch.
2) The employee bash script jogging on the example:
This script polls the SQS queue every 5 seconds for new messages and is in charge of following activities:
- Fetching Dynamic Directory join credentials (consumer title and password) from Techniques Manager.
- If the remote control EC2 example is running Windows, operating the Invoke-Command PowerShell cmdlet on the example to execute the Active Directory join procedure.
- If the remote control EC2 example is running Linux, working realm join command on the example to execute the Active Directory join procedure.
- Running the Remove-ADComputer order to eliminate the computer object through the Energetic Directory domain to get terminated EC2 occasions.
- Storing domain-became a member of EC2 instance details-computer title and IP address-within an Amazon DynamoDB table. This info are accustomed to check if an example is already area of the domain so when removing the example from the Energetic Directory domain.
More information
You have tested the perfect solution is now, here are a few additional points to end up being noted:
-
- The Dynamic Directory unjoin and join scripts given this solution could be replaced together with your existing custom scripts.
update the scripts in the worker example
- To, you need to upload the modified scripts to the S3 bucket and the noticeable changes will automatically synchronize on the instance.
- This solution works together with single account, Region, and VPC combination. It could be modified to utilize across a number of VPC and Regions mixtures.
- For VPCs in another Region or account, you need to share your AWS Managed Microsoft AD with another AWS accounts once the networking prerequisites have already been completed.
- The example user name and operating-system mapping used in the answer is founded on the default user name utilized by AWS.
- You may use AWS Systems Supervisor with VPC endpoints to get on EC2 instances that don’t have access to the internet.
The answer is protecting your Active Directory credentials and is ensuring:
- Energetic Directory credentials could be accessed just from the worker EC2 instance.
- The IAM role utilized by the employee EC2 example to fetch the trick can’t be assumed by some other IAM entities.
- Just authorized users can browse the credentials from the Secrets Manager console, through AWS CLI, or even by using any AWS Tool-such being an AWS SDK.
The focus of the solution would be to demonstrate a technique you may use to secure Active Directory credentials and automate the procedure of EC2 instances joining and unjoining from a dynamic Directory domain.
- You can associate the IAM plan named DENYPOLICY with any IAM team or even user in the account to block that user or even group from accessing or even modifying the worker EC2 example and the IAM role utilized by the worker.
- If your account belongs to a business, you may use an organization-level service control policy rather than an IAM-managed policy-like as DENYPOLICY-to protect the fundamental resources from unauthorized customers.
Conclusion
In this blog write-up, you learned how exactly to deploy an automated and secure solution through CloudFormation to greatly help secure the Dynamic Directory credentials and in addition manage adding and removing Amazon EC2 instances to and from a dynamic Directory domain. When working with this answer, you incur Amazon EC2 charges alongside charges connected with Secrets Manager pricing and AWS PrivateLink.
You can use the next references to greatly help diagnose or even troubleshoot common errors through the domain join or even unjoin process.
When you have feedback concerning this post, submit remarks in the Comments section below.
Want a lot more AWS Security how-to articles, news, and show announcements? Stick to us on Twitter.
