Automate Amazon EC2 example isolation through the use of tags
Containment is really a crucial component of a standard Incident Response Strategy, since this practice allows period for responders to execute forensics , recuperation and eradication during a good Incident. There are various techniques to containment. In this article, we will be concentrating on isolation-the capability to keep several targets separated in order that each target just sees and impacts itself-as a containment technique.
I’ll display you how exactly to automate isolation of an Amazon Elastic Compute Cloud (Amazon EC2) example through the use of an AWS Lambda functionality that’s set off by tag changes upon the example, as reported simply by Amazon CloudWatch Events .
CloudWatch Event Guidelines deliver the near real-time blast of system occasions that describe changes within Amazon Web Providers (AWS) resources. See furthermore Amazon EventBridge .
Finding your way through an incident is essential as outlined within the Safety Pillar of the AWS Well-Architected Framework.
From the 7 Design Concepts for Security within the Cloud, according to the Well-Architected Framework, this remedy covers the following:
-
- Enable traceability : Keep track of, alert, and audit modifications and actions to your atmosphere in real time. Integrate log and metric selection with systems to research and do something automatically.
-
- Automate security guidelines : Automatic software-based safety mechanisms can enhance your capability to securely scale quicker and cost-effectively. Create protected architectures, including via the implementation of regulates which can be managed plus defined by AWS because program code in version-controlled templates.
-
- Plan security activities : Plan an incident by applying incident administration and investigation plan and procedures that align to your organizational specifications. Run incident response make use of and simulations equipment with automation to greatly help boost your speed for detection, investigation, and recuperation.
After detecting a meeting in the Recognition analyzing and phase in the Analysis phase, you can automate the procedure of logically isolating an example from a Virtual Personal Cloud (VPC) in Amazon Internet Services (AWS).
In this blog write-up, I describe how exactly to automate EC2 instance isolation utilizing the tagging feature a responder can use to recognize instances that require to be isolated. A Lambda perform after that uses AWS API phone calls to isolate the situations by performing what described in the next sections.
Use situations
Your organization may use automated EC2 instance isolation for scenarios like these:
-
- A security analyst really wants to automate EC2 example isolation to be able to react to security events regularly.
-
- A protection manager wants to supply their very first responders with ways to quickly react to safety incidents without providing an excessive amount of usage of higher security functions.
High-level style and architecture
The example solution in this website post runs on the CloudWatch Events rule to trigger a Lambda function. The CloudWatch Events guideline is triggered whenever a tag is put on an EC2 example. The Lambda program code triggers further actions in line with the contents of the function. Remember that the CloudFormation template contains the correct permissions to operate the function.
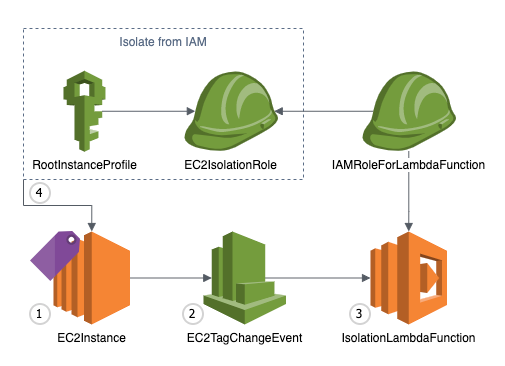
The function flow is demonstrated in Figure 1 and works the following:
-
- The EC2 example is tagged.
-
- The CloudWatch Events rule filter systems the event.
-
- The Lambda functionality is invoked.
-
- If the requirements are fulfilled, the isolation workflow starts.
Once the Lambda function is invoked and the criteria are met, these actions are performed:
-
- Checks for IAM example profile associations.
-
- If the example is related to a job, the Lambda functionality disassociates that part.
-
- Applies the isolation function that you described during CloudFormation stack development.
-
- Checks the VPC where in fact the EC2 instance resides.
-
- When there is no isolation security team in the VPC (if the VPC is fresh, for example), the event creates one.
-
- Checks the VPC where in fact the EC2 instance resides.
-
- Applies the isolation security team.
Take note : If you had a protection group having an open (0.0.0.0/0) outbound rule, which Isolation is applied by you security group, your existing SSH connections to the instance are dropped immediately. However, for those who have a narrower inbound principle which allows the SSH link initially, the existing connection will never be damaged by changing the mixed group. This is referred to as Link Tracking .

Figure 1: High-level diagram showing occasion flow
For the deployment technique, we will be utilizing an AWS CloudFormation Template. AWS CloudFormation offers you a good way to model an accumulation of associated AWS and third-party resources, provision them and consistently quickly, and manage them throughout their lifecycles, by dealing with infrastructure as code.
The AWS CloudFormation template that I provide here deploys the next resources:
-
- An EC2 instance part for isolation – that is mounted on the EC2 Example to avoid further communication with additional AWS Services hence limiting the attack surface area to your current infrastructure.
-
- An Amazon CloudWatch Events rule – that is utilized to detect adjustments to an AWS EC2 resource, in this whole case a “tag switch event”. We shall utilize this as a trigger to your Lambda function.
-
- An AWS Identification and Access Administration (IAM) function for Lambda functions – this is exactly what the Lambda function use to execute the workflow.
-
- A Lambda functionality for automation – this functionality is where all of the choice logic sits, as soon as triggered it shall follow a couple of steps described inside the next section .
-
- Lambda functionality permissions – that is utilized by the Lambda functionality to execute.
-
- An IAM example profile – it is a container for an IAM part which you can use to pass role details to an EC2 example.
Supporting features within the Lambda functionality
Let’s dive deeper into each helping function in the Lambda code.
The next function identifies the virtual private cloud (VPC) ID for confirmed instance. This is had a need to identify which safety groups can be found in the VPC.
The next function modifies the security band of an EC2 instance.
The next function creates a security group on a VPC that blocks all egress usage of the security group.
Deploy the perfect solution is
To deploy the answer provided in this website post, very first download the CloudFormation template, and create a CloudFormation stack that specifies the tags which are used to result in the automated process.
Download the CloudFormation template
To begin with, download the CloudFormation template from Amazon S3 . Additionally, you can start the CloudFormation template by choosing the following Start Stack key:

Deploy the CloudFormation stack
Begin by uploading the CloudFormation template to your AWS accounts.
To upload the template
-
- From the AWS Administration Console, open up the CloudFormation system.
-
- Choose Create Stack .
-
- Select With brand-new resources (regular) .
-
- Select Upload a template document .
-
- Select Choose Document , and choose the YAML file which you downloaded then.

Figure 2: CloudFormation stack development
Specify stack details
It is possible to leave the default values for the stack provided that there aren’t any sources provisioned already with exactly the same name, such as for example an IAM role. For instance, if still left with default ideals an IAM function named “SecurityIsolation-IAMRole” will undoubtedly be created. Or else, the naming convention will be fully customizable out of this screen and you will enter the selection of title for the CloudFormation stack, and change the parameters as you notice fit. Figure 3 displays the parameters that you could set.
The Evaluation Parameters section defines the tag key and value which will initiate the automated response. Remember that these ideals are case-sensitive.

Figure 3: CloudFormation stack parameters
Choose Next and soon you reach the ultimate screen, shown in Number 4, where you acknowledge an IAM role is established and you rely on the foundation of this template. Choose the check box close to the declaration I acknowledge that AWS CloudFormation might create IAM assets with custom brands , and choose Create Stack then.

Figure 4: CloudFormation IAM notification
After these actions are completed by you, the following sources will undoubtedly be provisioned, as proven in Figure 5:
-
- EC2IsolationRole
-
- EC2TagChangeEvent
-
- IAMRoleForLambdaFunction
-
- IsolationLambdaFunction
-
- IsolationLambdaFunctionInvokePermissions
-
- RootInstanceProfile

Figure 5: CloudFormation created assets
Testing
To start out your automation, tag an EC2 instance utilizing the tag defined through the CloudFormation set up. If you’re utilizing the Amazon EC2 gaming console, it is possible to apply tags to sources utilizing the Tags tab on the appropriate resource display, or you should use the Tags display screen, the AWS CLI or an AWS SDK. An in depth walkthrough for every approach are available in the Amazon EC2 Documentation web page .
Reverting Adjustments
If you want to remove the limitations applied by this workflow, complete the next steps.
-
- From the EC2 dashboard, in the Instances area, check the box close to the instance you wish to modify.

Figure 6: Choose the instance to change
- From the EC2 dashboard, in the Instances area, check the box close to the instance you wish to modify.
-
- In the very best right, select Activities , select Instance configurations , and then select Modify IAM part .
 Instance configurations > Modify IAM function” width=”500″ height=”478″>
Instance configurations > Modify IAM function” width=”500″ height=”478″>Shape 7: Choose Activities > Instance configurations > Modify IAM part
- In the very best right, select Activities , select Instance configurations , and then select Modify IAM part .
-
- Under IAM function , pick the IAM role to add to your instance, and choose Save then.

Figure 8: Pick the IAM role to add
- Under IAM function , pick the IAM role to add to your instance, and choose Save then.
-
- Select Activities , select Networking , and choose Modify security groups .
 Networking > Change safety groups” width=”500″ elevation=”415″>
Networking > Change safety groups” width=”500″ elevation=”415″>Figure 9: Choose Activities > Networking > Alter security groups
- Select Activities , select Networking , and choose Modify security groups .
-
- Under Associated protection groups , choose Get rid of and put in a different security team with the accessibility you would like to grant to the instance.
Summary
Utilizing the CloudFormation template supplied in this website post, a Security Functions Center analyst may have just tagging privileges plus isolate an EC2 example predicated on this tag. Or perhaps a security services such as for example Amazon GuardDuty could result in a lambda to use the tag within a workflow. This implies the Security Operations Middle analyst wouldn’t require administrative privileges on the EC2 service.
An isolation is established by this solution security team for any brand new VPCs that don’t have 1 already. The security team would follow the naming convention defined through the CloudFormation stack launch nevertheless, but won’t participate the provisioned assets. If you opt to delete the stack, guide cleanup would be necessary to get rid of these security groups.
This solution terminates established inbound Secure Shell (SSH) sessions which are associated to the instance, and isolates the example from new connections either outbound or inbound. For outbound connections which are already established (for instance, invert shell), you either have to turn off the network interface cards (NIC) at the operating-system (OS) degree, restart the instance system stack at the Operating system level, terminate the set up connections, or apply a system access control list (system ACL).
For more information, start to see the following documentation:
For those who have feedback concerning this post, submit remarks in the Comments area below.
Want a lot more AWS Security how-to articles, news, and show announcements? Stick to us on Twitter .

You must be logged in to post a comment.