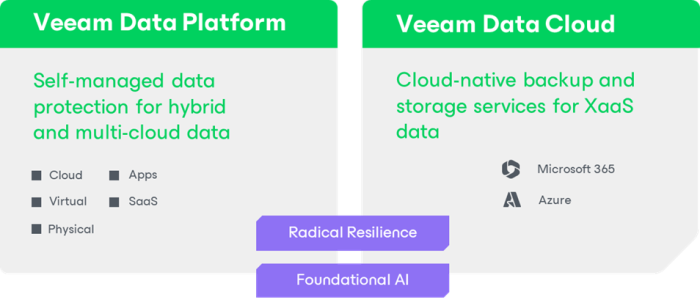
Veeam has 18+ years of history delivering market-leading data protection and ransomware recovery solutions. We have always been dedicated to providing our customers with freedom of choice within our product set, and this commitment has led us to an important milestone in our history. Today, we announce Veeam Data Cloud, providing resilient data protection and […]
Read more



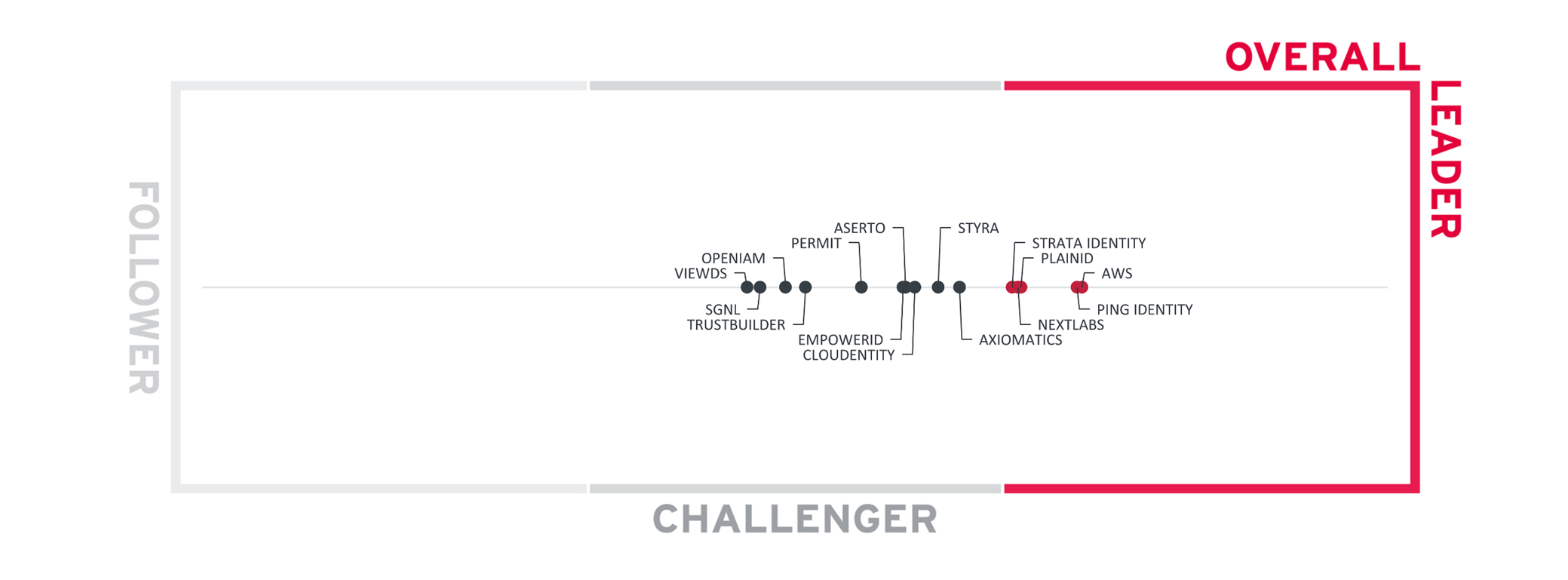
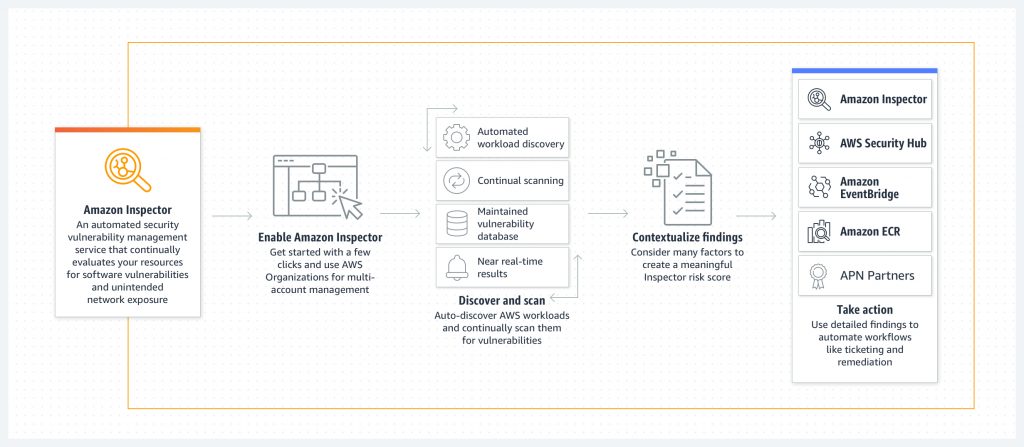
You must be logged in to post a comment.