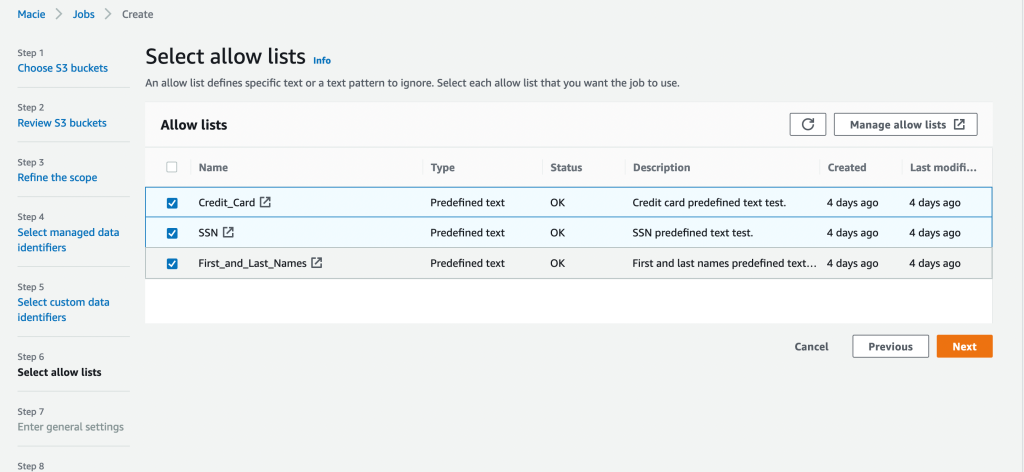
<a href=”https://aws.amazon.com/macie/” target=”_blank” rel=”noopener noreferrer”> Amazon Macie </a> is really a fully managed information security and data personal privacy service that utilizes machine learning and design matching to find and assist you to protect your sensitive information in <a href=”https://aws.amazon.com/” target=”_blank” rel=”noopener noreferrer”> Amazon Web Providers (AWS) </a> . The info that is available inside […]
Read more






You must be logged in to post a comment.